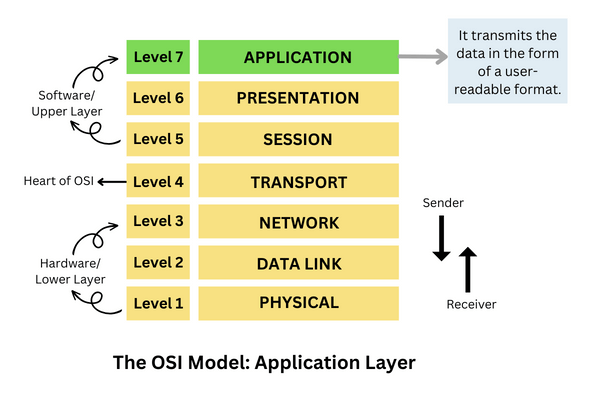
As we embark on the final leg of our OSI (Open Systems Interconnection) model expedition, we find ourselves at the pinnacle the Application Layer. Serving as the interface between the user and the network, the Application Layer encapsulates the software applications and network services that enable communication between devices. Before deep drive in Application layer, let's look on all previous layer in sort......
Recap: The OSI Model Overview Before diving into the intricacies of the Application Layer, let's briefly recap the other layers of the OSI model:
-
Physical Layer: The foundation, dealing with the physical connection and transmission of raw binary data over a physical medium.
-
Data Link Layer: Responsible for creating a reliable link between two directly connected nodes, ensuring error detection and correction.
-
Network Layer: Focuses on routing and logical addressing, allowing data to be sent from the source to the destination across multiple networks.
-
Transport Layer: Manages end-to-end communication, ensuring data integrity and reliability through mechanisms like flow control and error recovery.
-
Session Layer: Facilitates, manages, and terminates communication sessions, providing dialog control and synchronization.
-
Presentation Layer: Handles the translation, encryption, and compression of data, ensuring that the data sent from the Application Layer is in a format understandable by both communicating systems.
-
Application Layer: Unveiling the User Interface to the Network Now, let's turn our attention to the crown jewel, the Application layer. The Application Layer is like your device's friendly receptionist. It welcomes your software applications, translates their needs, and sends them on a journey through the network. This layer is the closest to the end user and encompasses the protocols and services that directly interact with software applications. Here's a closer look at its key features:
7.1 Services Provided: The Application Layer offers a range of services to application processes. These services can include file transfers, email services, network virtual terminals, and more. It acts as the bridge, enabling communication between the user and the network.
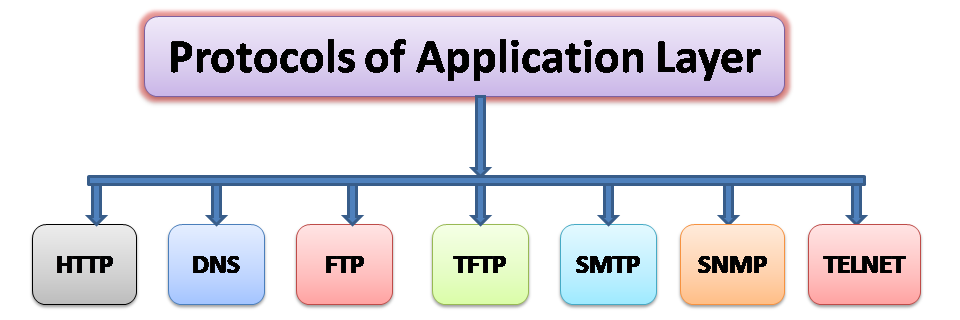
7.2 Protocols: Several protocols operate at the Application Layer, each catering to specific application-level functionalities. Common protocols include HTTP/HTTPS for web browsing, SMTP/POP3/IMAP for email communication, FTP for file transfer, and DNS for domain name resolution. Let's know each protocols in details:
-
Hypertext Transfer Protocol (HTTP):
- Purpose: HTTP is the foundation of any data exchange on the web. It's used for transferring hypertext (text with links, images, videos, etc.) between a web server and a web browser.
- Functionality: When you type a URL in your browser, it sends an HTTP request to the server, which responds with the requested web page.
-
Hypertext Transfer Protocol Secure (HTTPS):
- Purpose: Similar to HTTP but with an added layer of security. It encrypts the data exchanged between the browser and the server, ensuring a secure communication channel.
- Functionality: Used for secure transactions like online banking, shopping, and any other sensitive data transfer.
-
File Transfer Protocol (FTP):
- Purpose: FTP facilitates the transfer of files between computers on a network. It's commonly used for uploading website files to a server.
- Functionality: Users can upload, download, and manage files on a remote server using FTP clients.
-
Simple Mail Transfer Protocol (SMTP):
- Purpose: SMTP is the protocol for sending emails. It works between mail servers to deliver your emails to the recipient's mailbox.
- Functionality: When you hit 'send' on your email, SMTP takes care of routing it through the appropriate servers to reach the recipient.
-
Post Office Protocol (POP) and Internet Message Access Protocol (IMAP):
- Purpose: POP and IMAP are email retrieval protocols used by email clients to fetch messages from a mail server.
- Functionality: POP downloads emails to your device, while IMAP syncs your device with the server, allowing you to access emails from multiple devices.
-
Domain Name System (DNS):
- Purpose: DNS translates human-readable domain names into IP addresses. It's like a phonebook for the internet.
- Functionality: When you enter a URL, DNS translates it to an IP address, allowing your device to connect to the correct server.
-
Telnet:
- Purpose: Telnet allows remote access to other computers over a network.
- Functionality: Users can log into a remote computer and execute commands as if they were physically present.
-
Secure Shell (SSH):
- Purpose: Similar to Telnet but with added security. It provides a secure way to access a remote machine.
- Functionality: SSH encrypts the communication between the client and the server, preventing unauthorized access.
7.3 Interaction with Lower Layers: While the Application Layer is the uppermost layer, it relies on the services of the lower layers to ensure successful communication. Data is passed down the layers, encapsulated at each level, until it reaches the Physical Layer for transmission.
7.4 Examples of Application Layer Functions:
-
Web Browsing: HTTP (Hypertext Transfer Protocol) and HTTPS (Hypertext Transfer Protocol Secure) facilitate the transfer of web pages and related content.
-
Email Communication: SMTP (Simple Mail Transfer Protocol), POP3 (Post Office Protocol 3), and IMAP (Internet Message Access Protocol) govern the sending and retrieval of emails.
-
File Transfer: FTP (File Transfer Protocol) and SFTP (Secure File Transfer Protocol) enable the exchange of files between devices.
-
Domain Name Resolution: DNS (Domain Name System) translates user-friendly domain names into IP addresses, facilitating web requests.
-
Remote Access: Protocols like Telnet and SSH (Secure Shell) allow users to access remote systems and execute commands.
Conclusion: Wrapping Up the OSI Model Journey In concluding our exploration of the OSI model, we've unveiled the significance of each layer, from the foundational Physical Layer to the user-centric Application Layer. The model serves as a conceptual framework, guiding the development and understanding of network communication protocols.
Understanding the intricacies of the OSI model is crucial for network engineers, developers, and anyone involved in the world of networking. It provides a systematic approach to comprehending the complexities of communication systems, ensuring seamless and standardized interactions across diverse networks.
As we bid farewell to the OSI model journey, we carry with us a deeper appreciation for the layers that collectively shape the landscape of modern networking. Whether troubleshooting connectivity issues, designing robust applications, or optimizing network performance, the OSI model remains an invaluable tool in the arsenal of every IT professional.










0 Comments